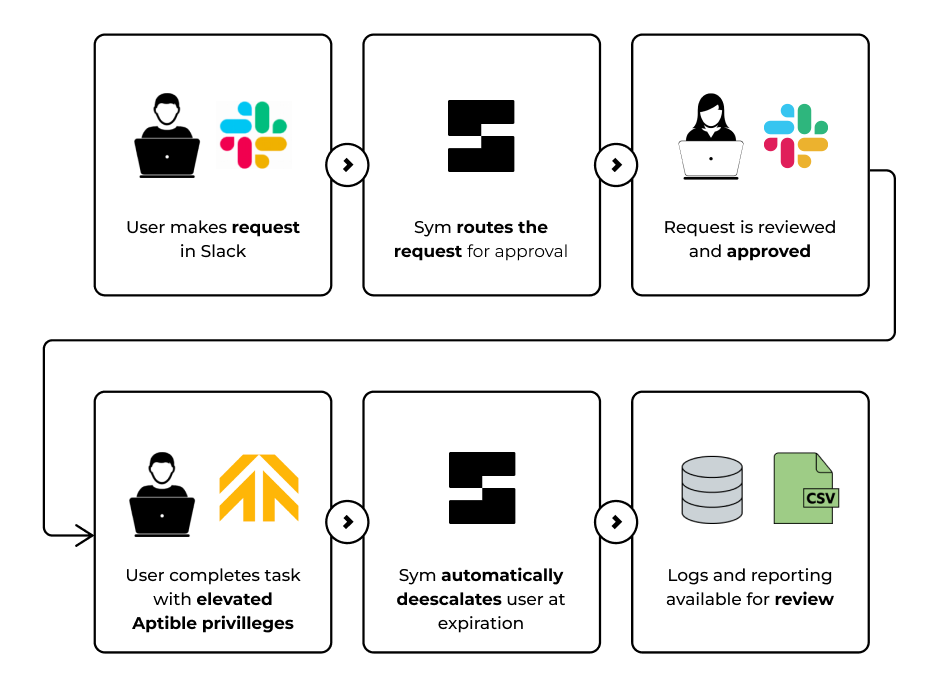
Aptible Access Strategy
With Sym and Aptible, you can get the benefits of flexible just-in-time role assignments and escalations with Aptible's secure PaaS tooling.
For example, Sym can help limit access to certain roles except when needed with approval. This will further improve your security posture by reducing default access and requiring approval for escalations.
Connect Sym with your AWS Secrets Manager
Follow the Manage Secrets with AWS Secrets Manager tutorial to connect your AWS Secrets Manager with the Sym Runtime.
Configure Aptible Bot User Credentials
-
Create a "bot" user for the integration. This bot will need to be granted Role Admin permissions. Sym will use these credentials to make API requests to Aptible.
-
Follow the Share Secrets with the Sym Runtime tutorial to share your Aptible Bot User credentials. We recommend using the JSON style secret to keep the username and password together.
{
"username": "[email protected]",
"password": "super-secret"
}
# Note: This example snippet shows only the Aptible specific resources.
resource "aws_secretsmanager_secret" "aptible_bot_credentials" {
name = "sym/main/aptible-bot-credentials"
description = "Username and password for Aptible Bot User"
tags = {
# This SymEnv tag is required and MUST match the SymEnv tag in the
# aws_iam_policy.secrets_manager_access in your `secrets.tf` file
SymEnv = local.environment_name
}
}
resource "sym_secret" "aptible_bot_username" {
# `sym_secrets` is defined in "Manage Secrets with AWS Secrets Manager"
source_id = sym_secrets.this.id
path = aws_secretsmanager_secret.aptible_bot_credentials.name
settings = {
json_key = "username" # The key to the bot user's username in your JSON secret
}
}
resource "sym_secret" "aptible_bot_password" {
# `sym_secrets` is defined in "Manage Secrets with AWS Secrets Manager"
source_id = sym_secrets.this.id
path = aws_secretsmanager_secret.aptible_bot_credentials.name
settings = {
json_key = "password" # The key to the bot user's password in your JSON secret
}
}
Add an Aptible Integration
Define a sym_integration resource with type = aptible. This integration will specify the bot user credentials, and will be referenced in the sym_strategy resource later.
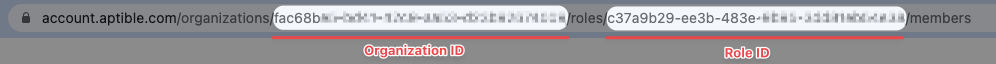
external_id: Your Aptible Organization ID. You can find it in the URL when logged in your Aptible dashboard. Example:https://account.aptible.com/organizations/**qac28b21-1234-5678-2a53-dq3s52272014**/usersusername_secret: A required setting which must be set to the ID of asym_secretreferencing your Aptible Bot Usernamepassword_secret: A required setting which must be set to the ID of asym_secretreferencing your Aptible Bot Password
resource "sym_integration" "aptible" {
type = "aptible"
name = "main-aptible"
# Your Aptible Organization ID
external_id = "94a49e57-d046-4d9d-9dbf-f7711e337368"
settings = {
# These secrets were defined in the previous step
username_secret = sym_secret.aptible_bot_username.id
password_secret = sym_secret.aptible_bot_password.id
}
}
Add Aptible Access Targets
Define sym_target resources with type = aptible_role for all of the Aptible Roles that you wish to manage access to.
You can find the role IDs by going to the Aptible dashboard and selecting a role. The ID will then be in the URL.
resource "sym_target" "admin_prod" {
type = "aptible_role"
name = "main-aptible-admin-role"
label = "Admin Role"
settings = {
role_id = "24463EF7-1D6E-402E-A365-69CB6DB80C6E"
}
}
resource "sym_target" "admin_ro" {
type = "aptible_role"
settings = {
role_id = "C7D5F21A-1D4E-4B39-9957-F8ACABDE2A3A"
}
}
Add an Aptible Access Strategy
Define a sym_strategy resource with type = aptible and include the Aptible Integration and Aptible Access Targets you defined above.
resource "sym_strategy" "this" {
type = "aptible"
name = "main-aptible-strategy"
# When this strategy is run, Sym Runtime will use the credentials specified
# in this integration to call Aptible APIs.
integration_id = sym_integration.aptible.id
# These are the targets that will be listed when a Flow with this strategy is run.
targets = [sym_target.admin_prod.id, sym_target.admin_ro.id]
}
Add the Aptible Strategy to your Flow
In your sym_flow resource, reference your Aptible sym_strategy as the strategy_id in your Flow Parameters.
resource "sym_flow" "this" {
name = "aptible_access"
label = "Aptible Access"
# ... other Flow attributes not shown
params {
# The strategy this Flow will use to manage access.
strategy_id = sym_strategy.aptible.id
# ... other Flow parameters not shown
}
}
Aptible Identity Management
| Identifier format | Example value |
|---|---|
| UUID | a59d7542-2346-4196-834d-d08af3e549c2 |
Sym will try to automatically discover user identities using their Sym email. In the case that a user's Sym email does not match their Aptible email, you might want to consider implementing a get_identity reducer, or manually populating it with symflow CLI. For more information on how Sym handles identities, check out the Managing User Identity page!
Full Example
You can find the complete code for this example in our Aptible Access Strategy Example.
Updated 4 months ago
