Security at Sym
Internal security program
We maintain a strong internal security program, including an annual SOC2 Type II audit, which you can read more about on our main security page.
Sym and your data
Sym’s hosted platform minimizes the collection and storage of sensitive data about the target systems that you integrate with us. We collect the basic user information and account configuration data that we need to act on escalation requests, and that's it.
Secrets
Sym does not store secrets in our platform, instead, we use cross-account AWS IAM permissions to access secrets that you manage in AWS Secrets Manager. Sym only works with your secrets in memory, at the point where we establish connections to your target systems. Read more in our Secrets Management section.
Integration data
Sym stores configuration data about the account ids and target resources that you integrate, such as Okta group IDs or AWS permission set ARNs.
User data
Sym stores basic identity information about the users that make and approve requests, including email and profile attributes. Sym will attempt to automatically fetch and store matching user identities from the systems you integrate using our identity discovery system.
Request data
Sym stores the data that users input in their request flows, such as the reason for making a request. Your company policy governs the types of data that users can input into these request flows.
Sym and your AWS environment
Sym assumes limited-scope IAM Roles in your AWS environment during execution. You can grant these roles specific capabilities depending on what your flows need:
- Access secrets in AWS Secrets Manager that have a certain tag (
SymEnvby default). - Assume other Sym IAM Roles (such as the IAM connector) to support a Sym Strategy.
- Ship data to a reporting destination if you enable one of Sym’s AWS Log Destinations.
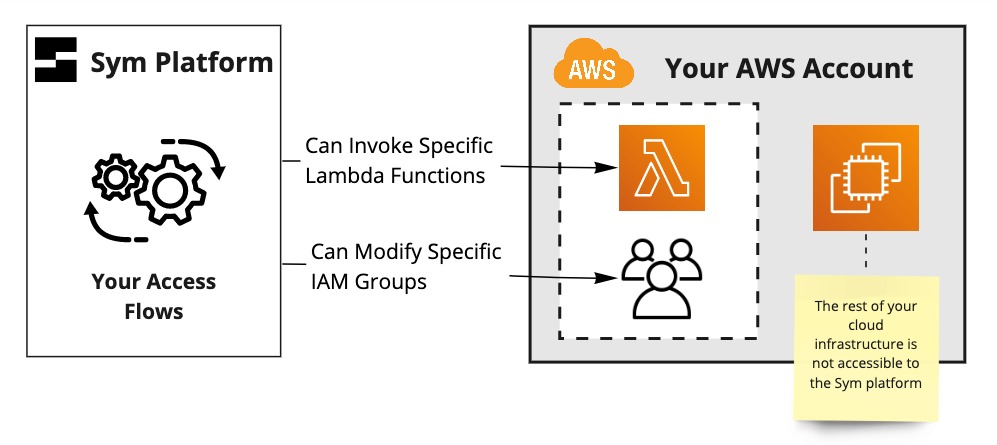
Sym IAM Roles define least privilege access to target services.
Cross-Account trust
Sym's IAM Role in your AWS account has a trust relationship with Sym's production AWS account. This trust relationship allows the Sym platform to securely assume your IAM role without a password. We use an External ID when assuming your IAM Role per AWS best practices.
What permissions does Sym need in my AWS account?
The minimum required permissions will depend on your use case. If you only need to use AWS to provide API keys (e.g. for our Okta Access Strategy), Sym will only need permissions to retrieve secrets specifically tagged for Sym.
If you want to use Sym to integrate with other AWS Services like IAM Identity Center (SSO), then you'll need to include additional connectors to grant these privileges.
You control Sym provisioning
You always have complete control over when, where, and how Sym resources are provisioned in your account. You can review the source code as well as the Terraform plans these modules produce before applying them.
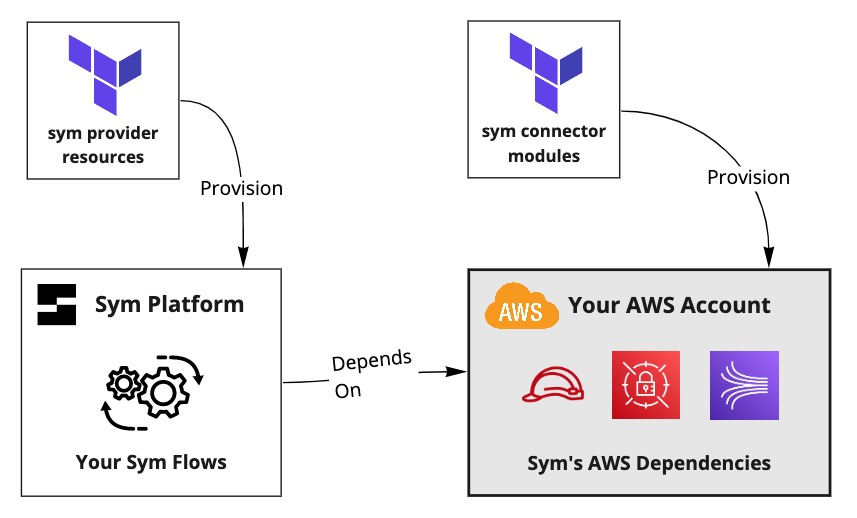
Sym's Terraform Provider provisions resources in the Sym Platform.
Connector modules provision resources in your environment.
Updated 5 months ago
